Java Environment:
1. Create a Maven Project
2. Import Dependencies
redis.clients jedis 4.3.2
Here, Jedis is used (providing APIs highly consistent with Redis commands)
3. Configure Port Forwarding
Prevent Redis port from being attacked by hackers; Map the Redis port of the cloud server to the local host.
Configuring in xshell:
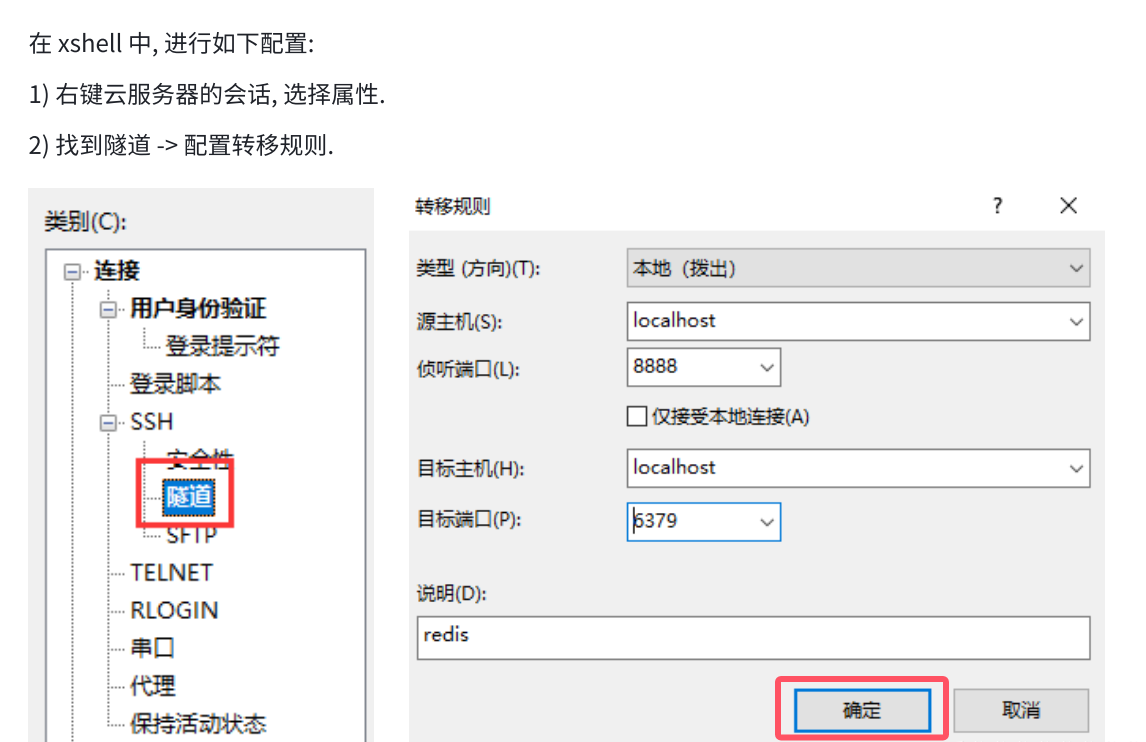
At this point, accessing the local port 8888 is equivalent to accessing the server’s port 6379.
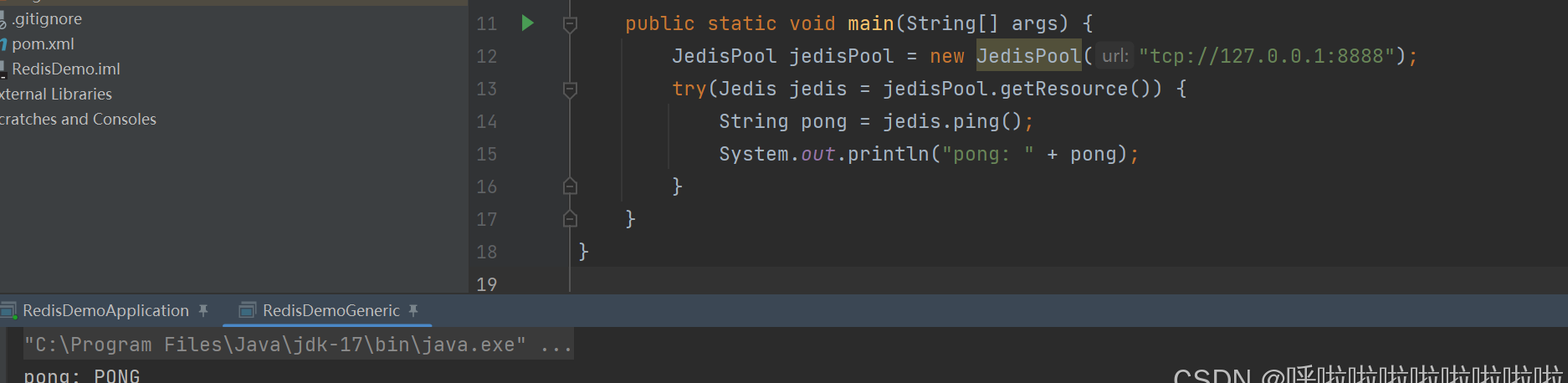
Connection successful at this point.
I. Basic commands:
public static void test(Jedis jedis) {
System.out.println("Set and get usage");
// Clear the database
jedis.flushAll();
jedis.set("key","k1");
jedis.set("key2","k2");
jedis.set("key3","k3");
String key = jedis.get("key");
String key2 = jedis.get("key2");
String key3 = jedis.get("key3");
System.out.println("key: " + key);
System.out.println("key2: " + key2);
System.out.println("key3: " + key3);
System.out.println("exists and del usage");
boolean result = jedis.exists("key");
System.out.println("result:" + result);
result = jedis.exists("key1111");
System.out.println("result:" + result);
long del = jedis.del("key", "key2");
result = jedis.exists("key");
System.out.println("result:" + result);
System.out.println("keys usage");
jedis.set("key","k1");
jedis.set("key2","k2");
Set<String> keys = jedis.keys("*");
System.out.println("keys: " + keys);
System.out.println("expire and ttl usage");
jedis.set("key4","k4");
jedis.expire("key4",10);
// Sleep for 5 seconds
try {
Thread.sleep(5000);
} catch (InterruptedException e) {
throw new RuntimeException(e);
}
long ttl = jedis.ttl("key4");
System.out.println("ttl: " + ttl );
System.out.println("type usage");
jedis.flushAll();
jedis.set("String", "1");
String type = jedis.type("String");
System.out.println("type: "+type);
jedis.lpush("list","111","222","333");
type = jedis.type("list");
System.out.println("type: "+type);
jedis.sadd("set","a","b","c");
type = jedis.type("set");
System.out.println("type: "+type);
jedis.zadd("zset",1.0,"zhangsan");
type = jedis.type("zset");
System.out.println("type: "+type);
jedis.hset("hash","f1 ","v1");
type = jedis.type("hash");
System.out.println("type: "+type);
}

String :
public static void test(Jedis jedis) {
// Clear the database
jedis.flushAll();
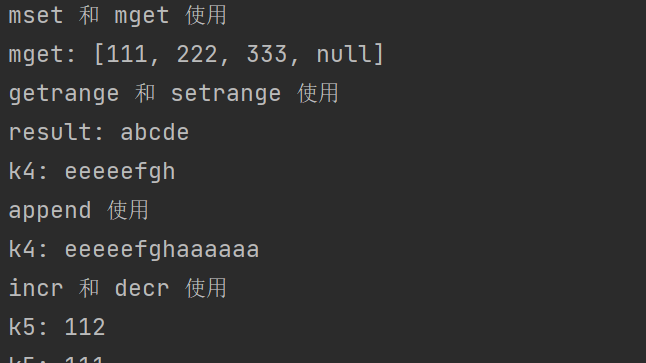
System.out.println("Using mset and mget");
jedis.mset("k1","111","k2","222","k3","333");
List<String> mget = jedis.mget("k1", "k2", "k3","k4");
System.out.println("mget: " +mget);
System.out.println("Using getrange and setrange");
jedis.set("k4","abcdefgh");
String k4 = jedis.getrange("k4", 0, 4);
System.out.println("result: " +k4);
jedis.setrange("k4",0,"eeee");
System.out.println("k4: " +jedis.get("k4"));
System.out.println("Using append");
jedis.append("k4","aaaaaa");
System.out.println("k4: " + jedis.get("k4"));
System.out.println("Using incr and decr");
jedis.set("k5","111");
System.out.println( "k5: " + jedis.incr("k5"));
System.out.println( "k5: " + jedis.decr("k5"));
}
List usage:
public static void test(Jedis jedis) {
jedis.flushAll();
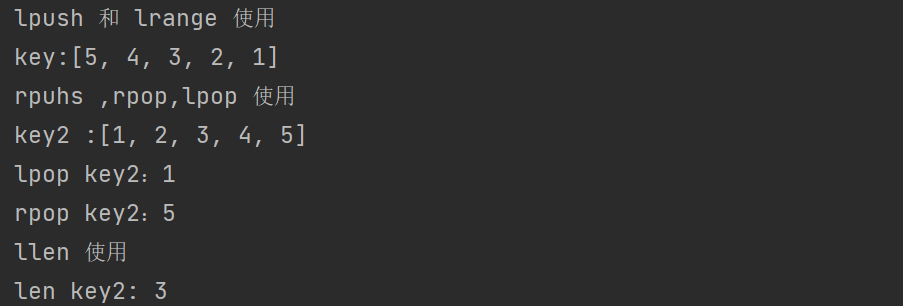
System.out.println("Using lpush and lrange");
jedis.lpush("key","1","2","3","4","5");
System.out.println("key:" + jedis.lrange("key",0,-1));
System.out.println("Using rpuhs, rpop, lpop");
jedis.rpush("key2","1","2","3","4","5");
System.out.println("key2 :" + jedis.lrange("key2",0,-1));
System.out.println("lpop key2:" + jedis.lpop("key2"));
System.out.println("rpop key2:" + jedis.rpop("key2"));
System.out.println("Using llen");
System.out.println("len key2: " + jedis.llen("key2"));
}
Hash usage:
private static void test(Jedis jedis) {
jedis.flushAll();
System.out.println("hset and hget usage");
HashMap<String,String> hash = new HashMap<>();
hash.put("f2","v2");
hash.put("f3","v3");
hash.put("f4","v4");
jedis.hset("key",hash);
jedis.hset("key","f1","v1");
System.out.println("key f1: " + jedis.hget("key", "f1"));
System.out.println("key f5: " + jedis.hget("key", "f5"));
System.out.println("hexists usage");
Boolean result = jedis.hexists("key","f1");
System.out.println("key f1 result: " + result);
result = jedis.hexists("key","f5");
System.out.println("key f5 result: " + result);
System.out.println("hkeys and hvals usage");
Set<String> hkeys = jedis.hkeys("key");
System.out.println("hkeys: " + hkeys);
List<String> hvals = jedis.hvals("key");
System.out.println("hvals: " + hvals);
System.out.println("hdel usage");
jedis.hdel("key","f1");
result = jedis.hexists("key","f1");
System.out.println("key f1 result: " + result);
System.out.println("hmset and hmget usage");
List<String> hmget = jedis.hmget("key", "f1", "f2", "f3");
System.out.println("hmget key: " + hmget);
}

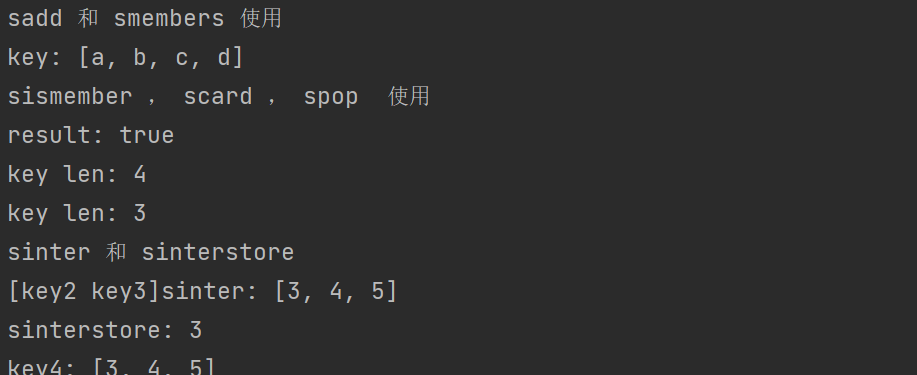
Usage of sets:
public static void test(Jedis jedis) {
jedis.flushAll();
System.out.println("sadd and smembers usage:");
jedis.sadd("key","a","b","c","d");
Set<String> smembers = jedis.smembers("key");
System.out.println("key: " +smembers);
System.out.println("sismember, scard, spop usage:");
boolean result = jedis.sismember("key", "a");
System.out.println("result: " + result);
long len = jedis.scard("key");
System.out.println("key len: " +len);
jedis.spop("key");
System.out.println("key len: " +jedis.scard("key"));
System.out.println("sinter and sinterstore usage:");
jedis.sadd("key2","1","2","3","4","5");
jedis.sadd("key3","3","4","5","6","7");
System.out.println("[key2 key3]sinter: "+ jedis.sinter("key2","key3"));
long sinterstore = jedis.sinterstore("key4", "key2", "key3");
System.out.println("sinterstore: " + sinterstore);
System.out.println("key4: " + jedis.smembers("key4"));
}
Usage of zset:
public static void test(Jedis jedis) {
jedis.flushAll();
System.out.println("Using zadd and zrange");
jedis.zadd("key",10.0,"zhangsan");
Map<String ,Double> hash = new HashMap<>();
hash.put("lisi",20.0);
hash.put("wangwu",30.0);
jedis.zadd("key",hash);
List<String> members = jedis.zrange("key", 0, -1);
System.out.println("members: "+members);
List<Tuple> key = jedis.zrangeWithScores("key", 0, -1);
System.out.println("key: " + key);
System.out.println("Using zcard and zscore");
long len = jedis.zcard("key");
System.out.println("len of key: " +len);
Double score = jedis.zscore("key","zhangsan");
System.out.println("score: " + score);
System.out.println("Using zrem and zrank");
Long zrank = jedis.zrank("key", "lisi");
System.out.println("rank of lisi: " + zrank);
jedis.zrem("key","zhangsan");
System.out.println("new rank of lisi: " + jedis.zrank("key", "lisi"));
}
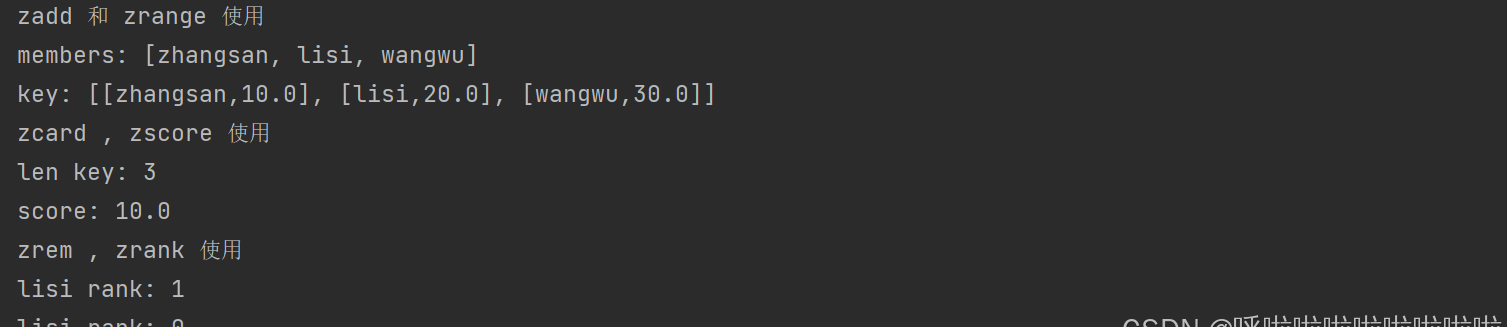
All are basic operations, similar to Redis operations.
Spring Environment:
Select during project creation

Obtain StringRedisTemplate via injection to operate Redis, equivalent to the previous Jedis.
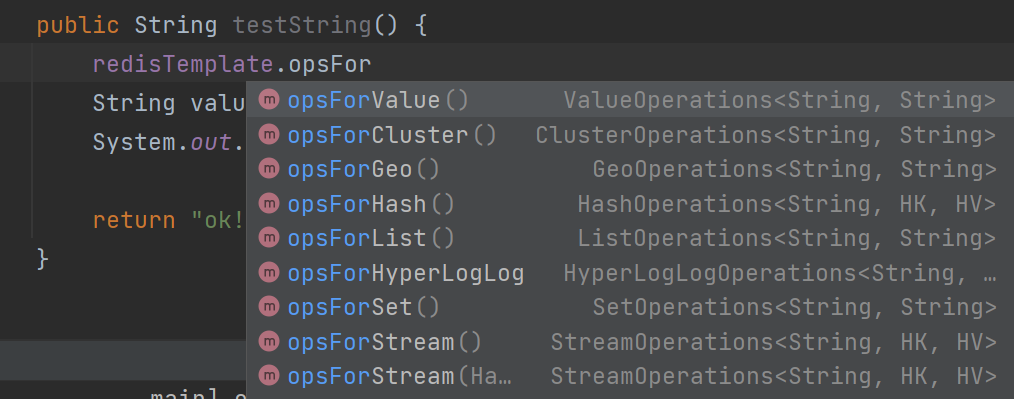
Categorizing methods for Redis operations to better organize them

Overall commands are largely consistent
Leave a Reply
You must be logged in to post a comment.